MQTT Security: Securing Mosquitto Server
This post describes how to implement MQTT security. In more details, we will describe how to securing Mosquitto MQTT server. As you may already know MQTT is one of the most important protocols widely used in Internet of things and in Industrial Internet of things. MQTT is a lightweight messaging oriented protocol where MQTT client exchanges messages through an MQTT server called MQTT broker. We have covered all the aspects about MQTT in a previous post named “MQTT protocol tutorial“.
In this post, we want to face the MQTT security aspects with a special regard to the aspects related to MQTT Mosquitto security.
Generally speaking, the Internet of things is the upcoming technological revolutions where objects, called smart objects, are connected to the internet exchanging data and information. One of the main concerns about Internet of things is the security aspect. Considering that IoT will impact our everyday lives and these smart objects are able to acquire and collect different kinds of information the security is an important aspect. Some of this information is sensitive (we can think about health data) and it is important to be sure that no one else can use it except the allowed persons and systems.
In this context, it is important to know how to securing MQTT protocol and how to protect the information. In the next paragraphs, we will analyze the steps we have to follow to secure MQTT using Raspberry Pi as MQTT broker.
WHAT DOES MQTT SECURITY MEAN?
By its nature, MQTT is a plain protocol that is all the information exchanged are in plain-text format. In other words, everyone could access to this message and read the payload. This could not be a problem if MQTT client and MQTT broker exchange not sensible information. Anyway, they are several use cases where we want to keep the information private and guarantee that it can not be read or modified during the transmitting process. In this case, there are several approaches we can use to face the MQTT security problem:
- Create a VPN between the clients and the server
- Use MQTT over SSL/TSL that encrypts and secure the information between the MQTT clients and MQTT broker
We will focus our attention on how to create an MQTT over SSL. To make MQTT a secure protocol we have to follow these steps:
- Create a private key (CA Key)
- Generate a certificate using the private key (CA cert)
- Create a certificate for Mosquitto MQTT server with the key
The final step is configuring Mosquitto MQTT so that it uses these certificates.
SECURING MOSQUITTO MQTT SERVER
The first step in this process is creating a private key. Connect to the Raspberry Pi using ssh or a remote desktop as you prefer and open a command terminal. Before starting is important you check OpenSSL is installed in your Raspberry Pi, otherwise, you have to download from here.
Before creating the private key, you should create a directory where you store all the certificates you will create. In the terminal write:
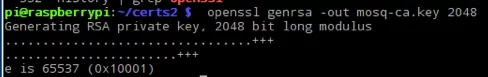
1 | openssl genrsa -out mosq-ca.key 2048 |
Using this command, we are creating a 2048 bit called mosq-ca.key. The result is shown in the picture below:
The nex step is creating a X509 certificate that uses the private key generated in the previous step. Open the terminal again and in the same directory you used to store the private key write:
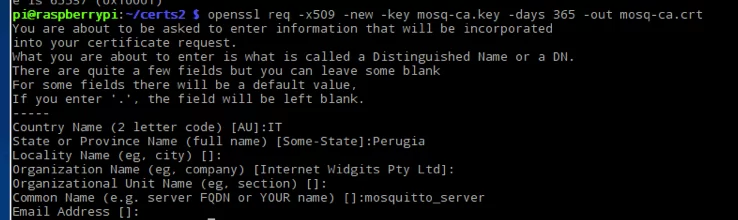
1 | openssl req -new -x509 -days365 -key mosq-ca.key -out mosq-ca.crt |
In this step, you have to provide different information before creating the certificate as shown in the picture below:
CREATING THE MQTT SERVER CERTIFICATE
Once the private key and the certificate are ready, we can move on and create the MQTT server certificate and private key:
1 | openssl genrsa -out mosq-serv.key 2048 |
Then the server certificate. During this step, we have to create a CSR (Certificate Signing Request). This certificate should be sent to the Certification authority that after verifying the author identity returns a certificate. In this tutorial, we will use a self-sign certificate:
1 | openssl req -new -key mosq-serv.key -out mosq-serv.csr |
As you can notice we have used the private key generated in the step before. Finally, we can create the certificate to use in our MQTT Mosquitto Server:
1 | openssl x509 -req -in mosq-serv.csr -CA mosq-ca.crt -CAkey mosq-ca.key -CAcreateserial -out mosq-serv.crt -days 365 -sha256 |
All done! We have completed the steps necessary to secure our MQTT server. You can verify your certificate writing:
1 | openssl x509 -in mosq-serv.crt -noout -text |
Now you should see the certificate.
HOW TO CONFIGURE MQTT MOSQUITTO SERVER TO SECURE MQTT
Once the certificates are ready, we have to configure MQTT Mosquitto server so that it can use these certificates. The certificates we have to use are:
- mosq-ca.crt
- mosq-serv.crt
- mosq-serv.key
Locate the mosquitto.conf file that holds all the configuration parameters and add the following lines:
1 2 3 4 | listener 8883cafile /home/pi/ssl-cert-mosq/mosq-ca.crtcertfile /home/pi/ssl-cert-mosq/mosq-serv.crtkeyfile /home/pi/ssl-cert-mosq/mosq-serv.key |
where the path /home/pi/ssl-cert-mosq is the path where you stored your certificate. Moreover, we change the default Mosquitto MQTT port to 8883.
Now you have to stop and restart Mosquitto MQTT so that it can read the new configuration file:
1 | sudo service mosquitto stop/start |
That’s all. Now our MQTT protocol is secure and encrypted. The last step is testing the configuration and the MQTT server.
MQTT SECURITY TESTING MOSQUITTO OVER SSL/TSL
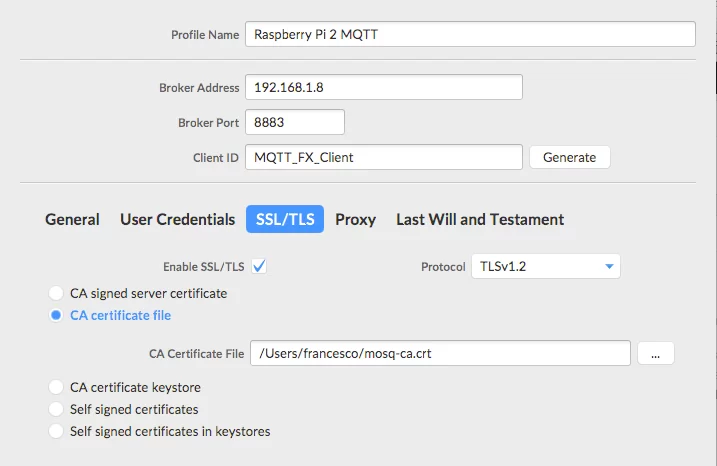
In this step, we will verify if the connection is correctly configured. To this purpose, we use MQTT.fx a java based MQTT client. After you installed it, we have to create a new profile providing all the information as shown in the picture below:
Notice that we have enabled the SSL/TSL configuration providing the mosq-ca.crt creating during the previous steps.
Finally, we can connect to the MQTT Mosquitto server:
clicking on connect. You will notice that the MQTT client will establish the connection to the MQTT broker as you can check in the log tab.
Now it is time to test if our client gets the message. Select the subscribe menu and subscribe the MQTT client to a topic (choosing a topic name).
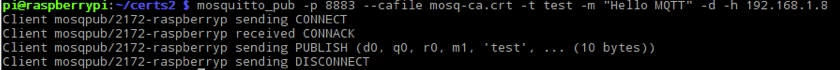
On the Raspberry Pi side lets us send a message on the same channel:
1 | mosquitto_pub -p 8883 -t "test" -cafile mosq-ca.crt -m "Hello MQTT" -d -h 192.168.1.8 |
The result is shown in the picture below:
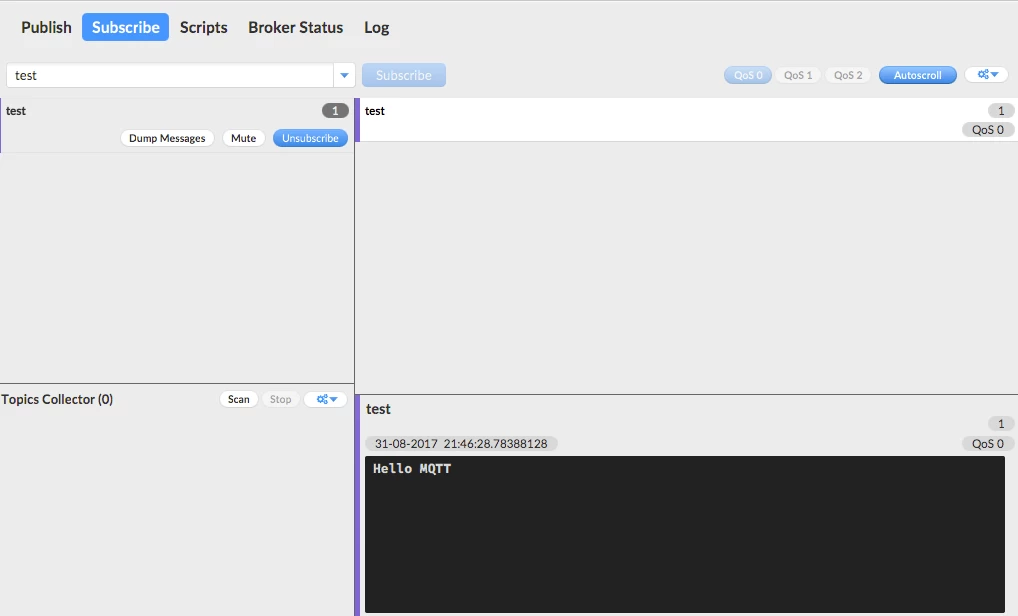
On the subscriber side we have:
As you can notice, we received the message sent by the publisher.
CONCLUSION
At the end of this post, you gained the knowledge about how to handle MQTT security configure Mosquitto MQTT over SSL/TSL.
| Reference: | MQTT Security: Securing Mosquitto Server from our JCG partner Francesco Azzola at the Surviving w/ Android blog. |




I’m trying to set-up Mosquitto with SSL on Raspberry Pi 3 following the tutorial. my mosquitto.conf in /etc/mosquitto/mosquitto.conf is: listener 8883 cafile /etc/mosquitto/certs/mosq-ca.crt certfile /etc/mosquitto/certs/mosq-serv.crt keyfile /etc/mosquitto/certs/mosq-serv.key But when I run the command: mosquitto_pub -p 8883 -t “test” –cafile /home/pi/mosq-cert/mosq-ca.crt -m “Hello MQTT” -d -h 10.xxx.x.x I get: Client mosqpub/5481-raspberryp sending CONNECT Error: A TLS error occurred. When I run the command sudo mosquitto -v (It will not listen to 8883) 1539177668: mosquitto version 1.4.10 (build date Wed, 17 Oct 2018 19:03:03 +0200) starting 1539177668: Using default config. 1539177668: Opening ipv4 listen socket on port 1883. 1539177668: Opening ipv6 listen… Read more »