Spring Boot 2 native approach to SSO with OAuth 2/OpenID Connect
This post is the final part of a 3 post series exploring ways to enable SSO with an OAuth2 provider for Spring Boot 2 based applications. The 3 posts are:
- Ways to bootstrap an OpenID Connect compliant OAuth2 Authorization Server/OpenID Provider
- Legacy Spring Boot/Spring 5 approach to integrating with an OAuth2 Authorization Server/OpenID Provider
- Newer Spring Boot 2/Spring 5 approach to integrating with an OAuth2 Authorization Server/OpenID Connect Provider – this post
This post will explore the shiny new way to enable SSO for a Spring Boot 2 application using the native OAuth2 support in Spring Security.
The post again assumes that everything described in the first post is completed.
Spring Boot 2 Auto-configuration
Spring Boot 2 provides an auto-configuration for native OAuth2 support in Spring Security ( see class org.springframework.boot.autoconfigure.security.oauth2.client.OAuth2ClientAutoConfiguration).
The auto-configuration is activated by the presence of “spring-security-oauth2-client” library available via the following gradle coordinates:
compile "org.springframework.security:spring-security-oauth2-client"
This auto-configuration works off a set of properties, for the UAA Identity provider that has been started up, the set of properties are the following:
uaa-base-url: http://localhost:8080/uaa
spring:
security:
oauth2:
client:
registration:
uaa:
client-id: client1
client-secret: client1
authorizationGrantType: authorization_code
redirect_uri_template: "{baseUrl}/login/oauth2/code/{registrationId}"
scope: resource.read,resource.write,openid,profile
clientName: oauth2-sample-client
provider:
uaa:
token-uri: ${uaa-base-url}/oauth/token
authorization-uri: ${uaa-base-url}/oauth/authorize
user-info-uri: ${uaa-base-url}/userinfo
jwk-set-uri: ${uaa-base-url}/token_keys
userNameAttribute: user_nameIf I were to depend on Spring Boot 2 auto-configuration support for native OAuth2 support to do its magic and were to start the application up, I would be presented with this page on accessing the application:
Note that this login page is a default page created by Spring Security OAuth2 and by default presents the list of registrations.
Clicking on “oauth2-sample-client” presents the login page of the Identity provider, UAA in this instance:
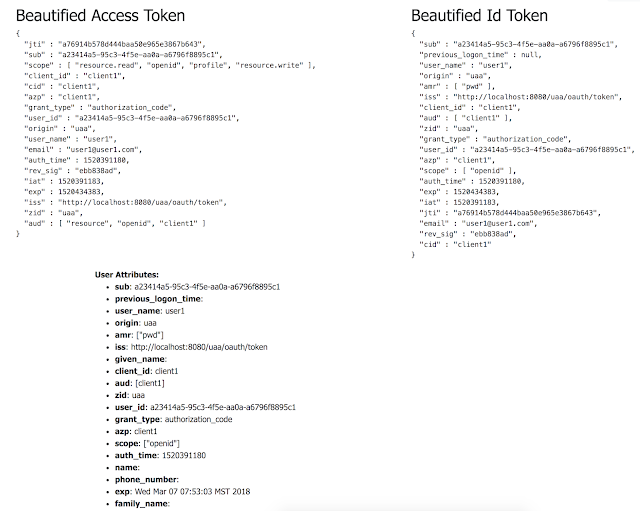
For an OpenID Connect based flow, applications are issued an ID Token along with an Access Token which I am decoding and presenting on a page:
Customizations
One of the quick customizations that I want to make is to redirect to UAA on access of any secured page specified via a “/secured” uri pattern, the following is a set of configuration that should enable this:
package sample.oauth2.config
import org.springframework.context.annotation.Configuration
import org.springframework.security.config.annotation.web.builders.HttpSecurity
import org.springframework.security.config.annotation.web.builders.WebSecurity
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter
@Configuration
class OAuth2SecurityConfig : WebSecurityConfigurerAdapter() {
override fun configure(web: WebSecurity) {
super.configure(web)
web.ignoring()
.mvcMatchers(
"/favicon.ico",
"/webjars/**",
"/css/**"
)
}
override fun configure(http: HttpSecurity) {
http.csrf().disable()
http.authorizeRequests()
.antMatchers("/secured/**")
.authenticated()
.antMatchers("/", "/custom_login")
.permitAll()
.anyRequest()
.authenticated()
.and()
.oauth2Login()
.loginPage("/custom_login")
}
}See the “/custom_login” being set as the URI above, which in turn simply hands over control to OAuth2 controlled endpoints which know to set the appropriate parameters and redirect to UAA:
@Controller
class LoginController {
@RequestMapping("/custom_login")
fun loginPage(): String {
return "redirect:/oauth2/authorization/uaa"
}
}This concludes the exploration of native OAuth2 support in Spring Boo2 applications.
All of the samples are available in my github repo – https://github.com/bijukunjummen/oauth2-boot2
The following references were helpful in understanding the OAuth2 support:
1.Spring Security Documentation – https://docs.spring.io/spring-security/site/docs/current/reference/html/
2.Joe Grandja’s Spring One Platform 2017 Presentation – https://www.youtube.com/watch?v=WhrOCurxFWU
| Published on Java Code Geeks with permission by Biju Kunjummen, partner at our JCG program. See the original article here: Spring Boot 2 native approach to SSO with OAuth 2/OpenID Connect Opinions expressed by Java Code Geeks contributors are their own. |






Hi, it does not work for me, it throws an exception because the algorithm used for the JWT issued by UAA is HS256, however, the expected is RS256, this is where it crashes:
NimbusReactiveJwtDecoder::decode()
can you fix the issue please?
Sorry for not giving details on which project, I tested all servers, no one works, the legacy project gives an error because it sets the redirect URI to /login, which is not the one registered at the UAA identity server, at the UAA we registered login/oauth2/code/uaa
The Webflux is the one that gives the JWK matcher can not be null (it expected RS256, not HS256), I would kindly ask you to please fix the issues and resubmit the projects, as for now, freshly cloned from git no one works …