Put Gosec in Your Pipeline to Spot Source Code Security Problems
Golang keeps trending up and to the right in programming language popularity, for many reasons. Great libraries, which means more users, which means more libraries and more users — more users like me who are prone to make mistakes.
To err is human, to forgive divine – Alexander Pope
Who can say at one time or another they haven’t accidentally checked in some hard coded password, or personal access token, or used an insecure random number seed. I know I have! Well I can tell you that whilst Alexander Pope says “to forgive divine,” sys admins and code reviewers do not think so kindly.
Not to worry, there is an open source tool called gosec which exists to help spot problems right in your Go source code. You can run this from your desktop/editor, or you can (and possibly) should put it as part of your pipeline (should the “unforgivable” happen).
Gosec works by loading up all your sourcecode into an AST, and applies a set of built in rules looking for common mistakes such as secrets in code (kind of neat: it looks for hi-entropy strings which usually mean a secret), SQL string assembly (a source of injection attacks) and more. If it gets a false positive, you can always add a comment telling it to skip it (maybe that string correcthorsebatterystaple89874328^&^&*^FDHJKHKJFDHJKS is actually a legitimate thing and not at all a secret).
Breaking your pipeline at the right time
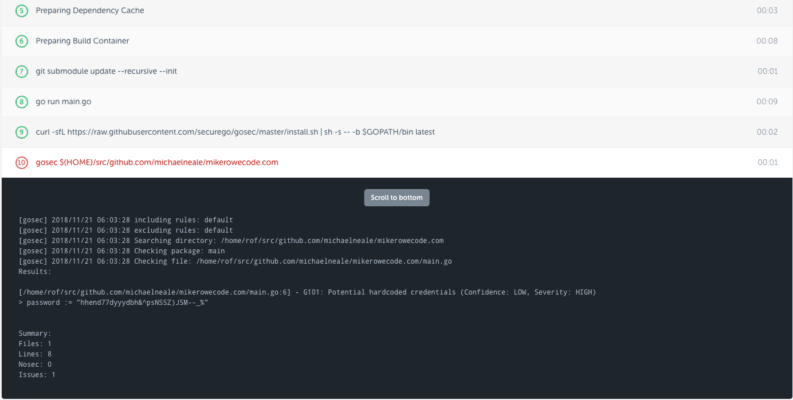
Once gosec is in your pipeline, should any rules be broken, your build will fail before too much harm is done. It looks like this:
(There are many formats you can report violations in – this is just the default, which seems fine to me).
Setting it up
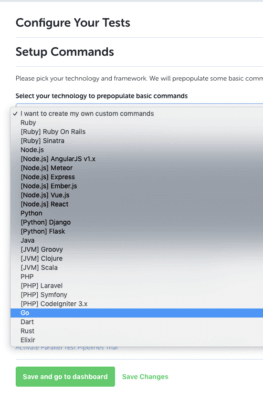
Using this in CloudBees CodeShip is super easy, of course. CloudBees CodeShip has some pretty good Golang support “out of the box”, so firstly create a new project:
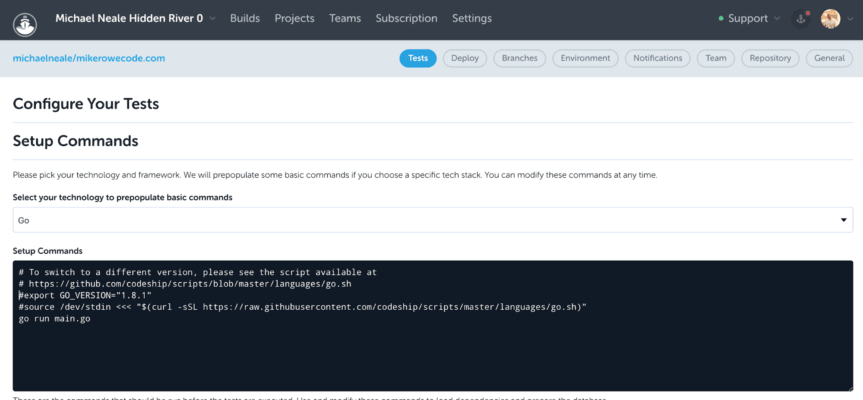
Next up, configure your build steps, you do what you need to do:
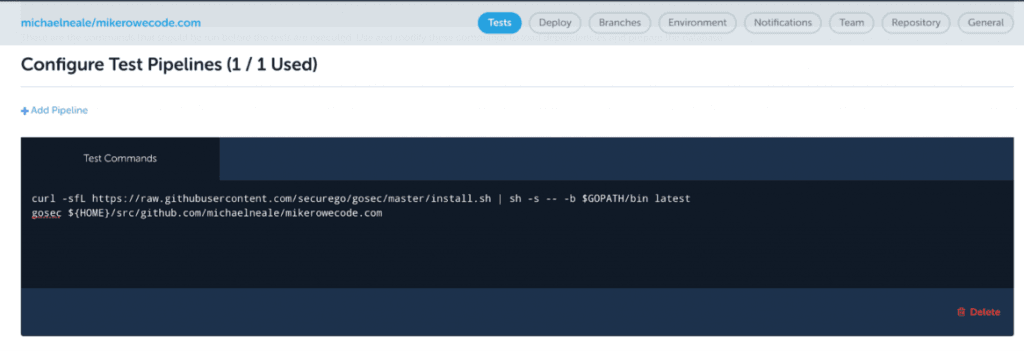
Then add in gosec as part of the test configuration:
curl -sfL https://raw.githubusercontent.com/securego/gosec/master/install.sh | sh -s -- -b $GOPATH/bin latest
gosec ${HOME}/src/github.com/michaelneale/mikerowecode.comThis will install the latest version of it (not a bad idea) and then apply the full set of rules. You can exclude specific rules on the command line (or you can annotate code in comments to ignore things that are false positives as needed).
Gosec works off source code and the AST, so it makes sense to do this before running tests to get that earlier feedback (you could possibly do it even before the build steps – although they may modify the source or bring in more, up to you really).
And that is it. Your day could be slightly less embarrassing.
Additional resources
- Read about using Go for development
- Learn about Go applications and Docker containers
- Register for the webinar on adding container security in the CodeShip pipeline with Anchore
| Published on Java Code Geeks with permission by Michael Neale, partner at our JCG program. See the original article here: Put Gosec in Your Pipeline to Spot Source Code Security Problems
Opinions expressed by Java Code Geeks contributors are their own. |