Understanding Transport Layer Security / Secure Socket Layer
Transport Layer Security (TLS) 1.0 / Secure Sockets Layer (SSL) 3.0, is the mechanism to provide private, secured and reliable communication over the internet. It is the most widely used protocols that provides secure HTTPS for internet communications between the client (web browsers) and web servers. It ensures that the transport of sensitive data are safe from cyber crimes which steals valuable client information. TLS/SSL enables server authentication, client authentication, data encryption, and data integrity over internet. Earlier most of the payment based web applications were involved in secured communication to prevent hacking and keep the critical payment information safe. The disadvantage of SSL is the performance hit. Since the data passed over the secured layer has to be encrypted by the server it uses more server resources than the unencrypted communication. However in recent days
with faster internet most of the authentication based web applications prefer secured HTTPS. E.g. Google, Facebook, Twitter etc. and HTTPS is not limited to e-commerce or banking websites only.
What is the difference between TLS and SSL?
There are subtle differences between TLS and SSL. TLS is the successor to the SSL but TLS 1.2 cannot be interchangeable with SSL 3.0. TLS uses Hashing for Message Authentication Code (HMAC) algorithm over the SSL Message Authentication Code (MAC) algorithm.
HMAC is more secured than the standard SSL MAC algorithm.
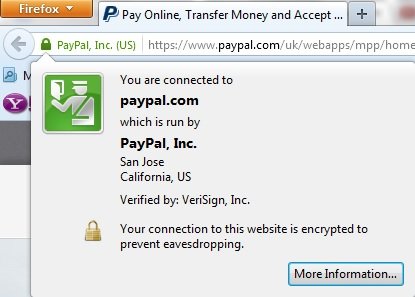
How to recognize a secured website?
Most of the browsers helps the visitors to identify if any website is secured by showing the ‘https’ in the address bar and also the certificate authority which has validated the website.
Before we explore on how SSL works let’s try to understand more about some of the key terminologies.
- Encryption – In cryptography terminology encryption is a process of encoding information which is sent from one computer to another in such a way that unauthorized persons cannot get access to the original data.
- Identification – Identification is a process through which one system confirms the identity of another person / entity/ computer system.
- Authentication – Authentication is a process to verify the credentials of the principal or the system. The JEE platform requires that all the application servers provide support for authentication mechanisms likes HTTP basic authentication, SSL mutual authentication, form based login.
- Authorization – It is a process by which the principal is either granted access or disallowed to protected resources. Only the trusted principal can be granted secure access.
Why do we need encryption?
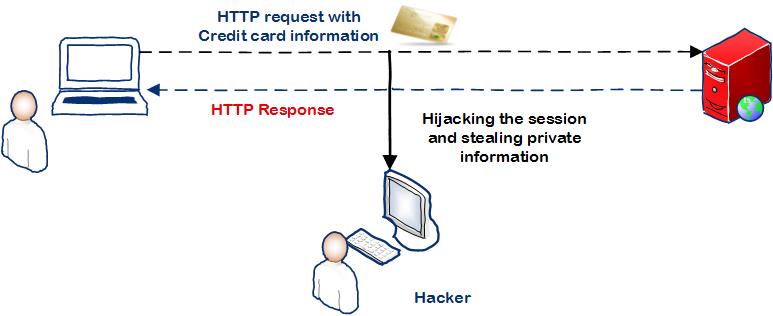
If we do not use encryption then the critical credit card information can be stolen by the unauthorised persons who might hijack the session between the client and server communication.
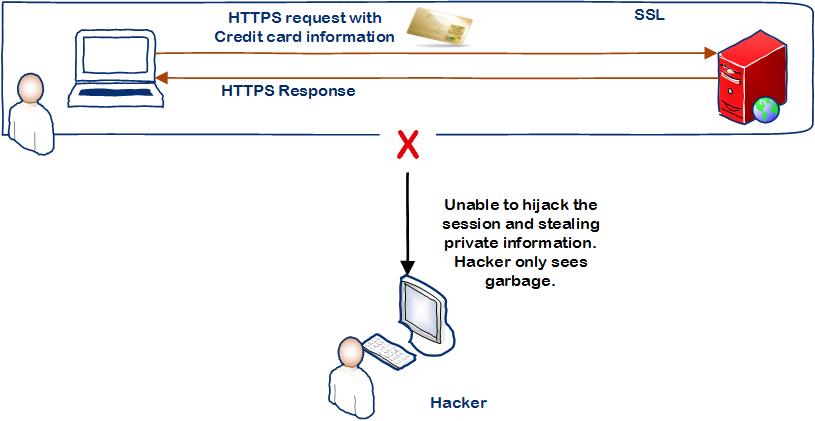
When we use encryption the credit card information are encrypted and it is passed through a secured HTTPS connection which prevents any hackers from unauthorized access of the data.
How does this Encryption process works between the client and server?
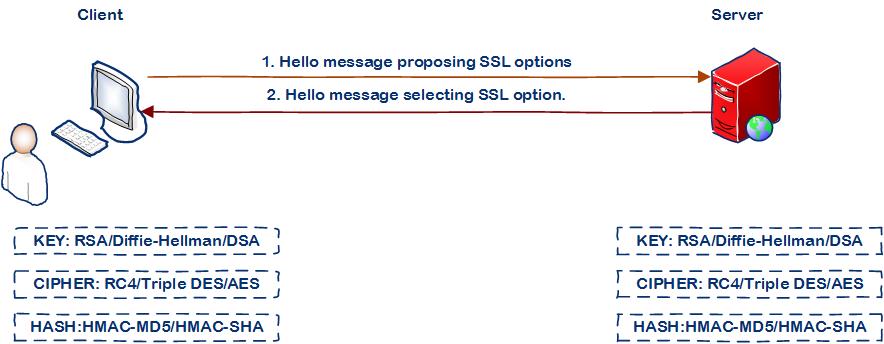
There are several steps before the actual encrypted message is sent. The first process starts with SSL Handshake or establishing a secured connection between the client and the server. This process requires total of nine handshake messages to be communicated between server and client. One the handshake is completed then encrypted messages are communicated between client and server.
One way SSL authentication
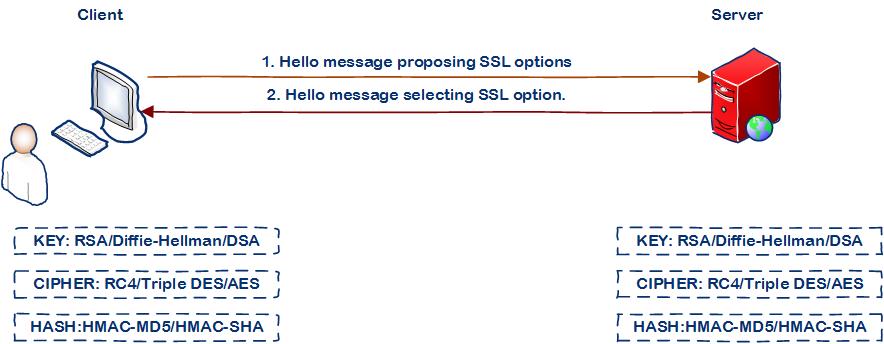
Step 1: Client and server agrees on the medium of encryption
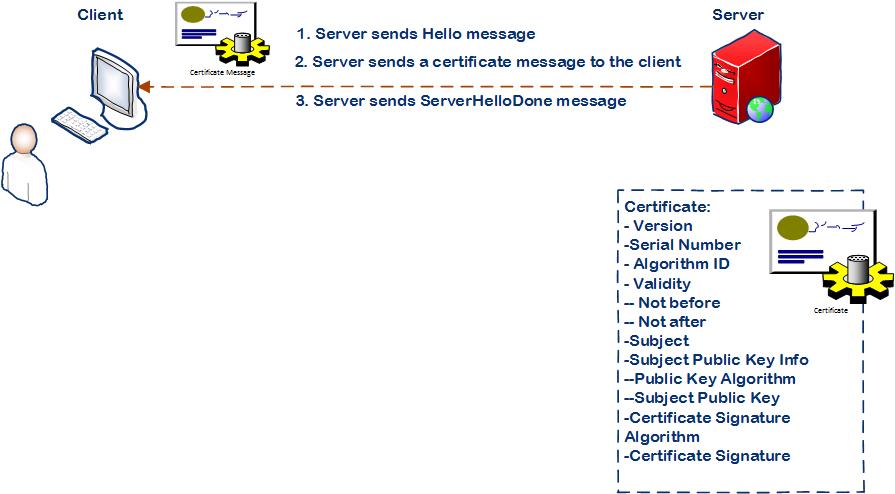
Step 2: Server sends a certificate message to the client
- Server sends Hello message to the client.
- Server sends a Certificate message to the client which consists of the server’s certificate including the server’s public key.
- Before the client computer requests to start encryption the server concludes its part of the negotiation with ServerHelloDone message.
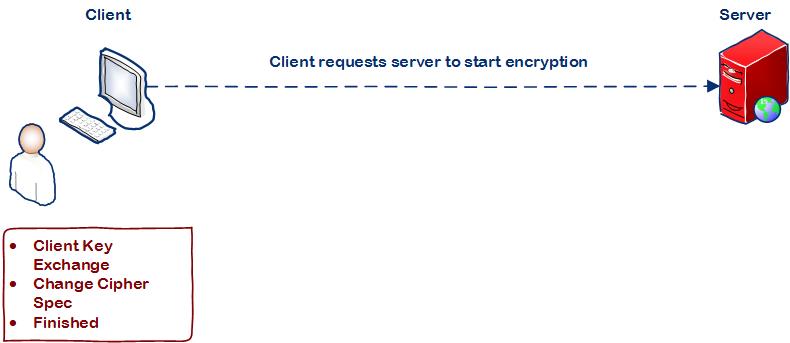
Step 3: Client computer requests to start encryption
Client then sends the session key information which is encrypted with server’s public key in the Client Key Exchange message. Both client and server calculates the master secret code and in future this code is used to encrypt the messages between the client and server.Client sends Change Cipher Spec message to activate the negotiated SSL encryption options which was agreed during the Hello message communication for all future messages it will send. And then the client requests finish which finally will request the server to start the encryption.
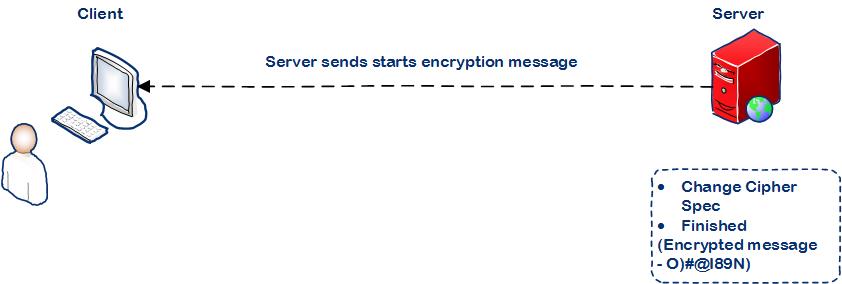
Step 4: Server confirms to start the encryption
Server sends Change Cipher Spec message to activate the previously negotiated options for all future messages it will send.
Server then sends the Finished message to the client and requests it to check the newly activated options. When the finished message is delivered it is sent in encrypted mode.
This completes all the handshake process.
Step 5: The messages are encrypted
Now the client and servers communicates securely through encrypted messages only.
Two way SSL communication (Mutual SSL Authentication)
Step 1: Client and server agrees on the medium of encryption
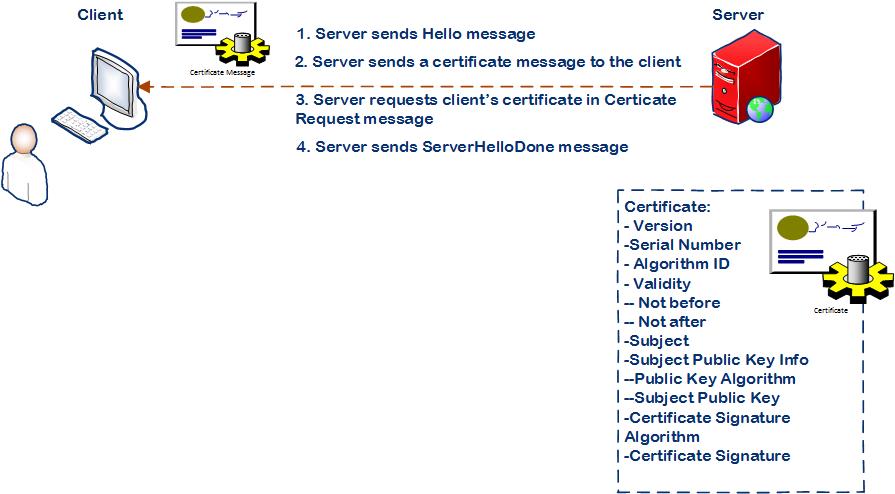
Step 2: Server sends a certificate message to the client
• Server sends Hello message to the client.
• Server sends a Certificate message to the client which consists of the server’s certificate including the server’s public key.
• Server requests client’s certificate in Certificate Request message, so that the connection can be mutually authenticated.
• Before the client computer requests to start encryption the server concludes its part of the negotiation with Server Hello Done message.
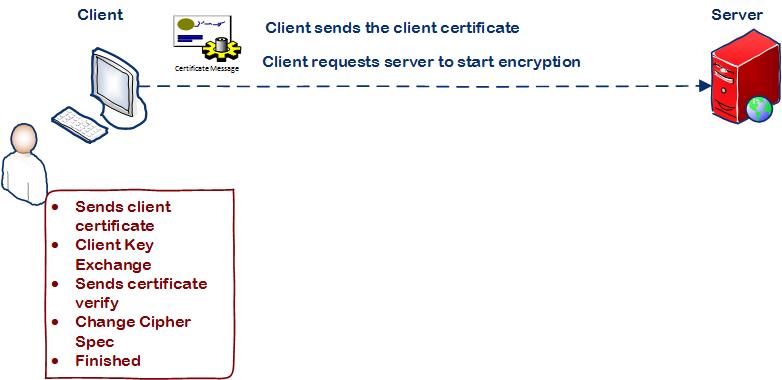
Step 3: Client computer requests to start encryption
• Client responds to the server with Certificate message, which contains the client’s certificate.
• Client then sends the session key information which is encrypted with server’s public key in the Client Key Exchange message.
• Client sends a Certificate Verify message to let the server know it owns the sent certificate. Both client and server calculates the master secret code and in future this code is used to encrypt the messages between the client and server.
• Client sends Change Cipher Spec message to activate the negotiated SSL encryption options which was agreed during the Hello message communication for all future messages it will send.
• And then the client requests finish which finally will request the server to start the encryption.
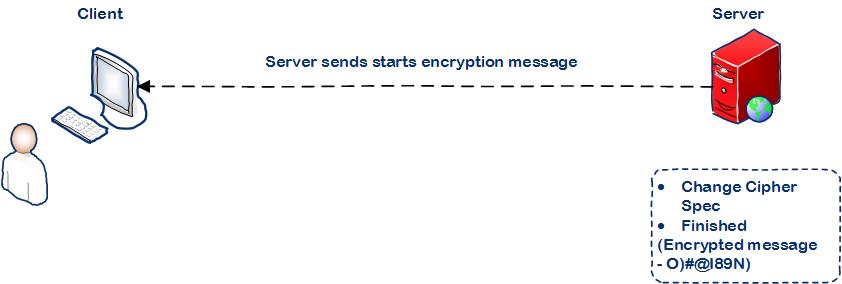
Step 4: Server confirms to start the encryption
Server sends Change Cipher Spec message to activate the previously negotiated options for all future messages it will send.
Server then sends the Finished message to the client and requests it to check the newly activated options. When the finished message is delivered it is sent in encrypted mode.
This completes all the handshake process.
Step 5: The messages are encrypted
Now the client and servers communicates securely through encrypted messages only.





Thanks lot.
How does this protect against a man-in-the-middle attack?